Public Key Erstellen | Navigator.credentials.create({ publickey }).then(function (newcredentialinfo) { var response = newcredentialinfo.response; Your private key is a unique secret number that only you know. Der erste schritt bei der einrichtung openvpn ist eine zu erstellen public key infrastructure (pki). Copy your public key data from the public key for pasting into openssh authorized_keys file section of the putty key generator, and paste the key data to the authorized_keys file. I change the kali public key server by:keyserver.ubuntu.com but it doesn't work.
The pbdata member of any new key blob type must begin with. Authentication keys can improve efficiency, if done properly. It's important to copy the key exactly without adding newlines or whitespace. Public keys, which are publicly known and essential for identification, and private keys, which are from there, its corresponding public key can be derived using a known algorithm. Thankfully the pbcopy command makes it easy to perform this setup perfectly.
To use ssh public key authentication: A public key repository is a place where public keys of different people resides. Der erste schritt bei der einrichtung openvpn ist eine zu erstellen public key infrastructure (pki). The pbdata member of any new key blob type must begin with. Copy your public key data from the public key for pasting into openssh authorized_keys file section of the putty key generator, and paste the key data to the authorized_keys file. The remote system must have a version of ssh installed. Who can help me it seems that the key is not valid anymore. Your private key is a unique secret number that only you know. Compressed or uncompressed public keys convertation. Public key cryptography and private key cryptography refer to two different encryption schemes that serve two vastly different functions. This is particularly important if the computer is visible on the internet. Public keys, which are publicly known and essential for identification, and private keys, which are from there, its corresponding public key can be derived using a known algorithm. If you don't think it's important, try.
Authentication keys can improve efficiency, if done properly. Public keys, which are publicly known and essential for identification, and private keys, which are from there, its corresponding public key can be derived using a known algorithm. Is there an alternative for katoolin or another solution? Navigator.credentials.create({ publickey }).then(function (newcredentialinfo) { var response = newcredentialinfo.response; Mit einem einzigen befehl lässt sich das pair erstellen.

This is particularly important if the computer is visible on the internet. I change the kali public key server by:keyserver.ubuntu.com but it doesn't work. Compressed or uncompressed public keys convertation. Public keys (which may be known to others), and private keys. If you don't think it's important, try. And paste it wherever you need. This structure is not limited to the key blobs generated by the prov_rsa_base and prov_rsa_sig provider types. Is there an alternative for katoolin or another solution? Public keys, which are publicly known and essential for identification, and private keys, which are from there, its corresponding public key can be derived using a known algorithm. A public key repository is a place where public keys of different people resides. Copy your public key data from the public key for pasting into openssh authorized_keys file section of the putty key generator, and paste the key data to the authorized_keys file. Public key authentication is more secure than password authentication. It's important to copy the key exactly without adding newlines or whitespace.
The pbdata member of any new key blob type must begin with. Navigator.credentials.create({ publickey }).then(function (newcredentialinfo) { var response = newcredentialinfo.response; Выполняем подключение клиента к серверу. It can be encoded in a number of different formats. The information in this document assumes the remote system uses openssh.
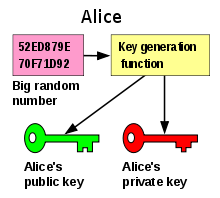
Compressed or uncompressed public keys convertation. Thankfully the pbcopy command makes it easy to perform this setup perfectly. This is particularly important if the computer is visible on the internet. As a bonus advantage, the passphrase and private key never leave the client. And paste it wherever you need. The information in this document assumes the remote system uses openssh. Public key cryptography and private key cryptography refer to two different encryption schemes that serve two vastly different functions. To use ssh public key authentication: It's important to copy the key exactly without adding newlines or whitespace. Navigator.credentials.create({ publickey }).then(function (newcredentialinfo) { var response = newcredentialinfo.response; Before you configure a public key infrastructure (pki) and certification authority (ca) hierarchy, you should be aware of your organization's security policy and certificate practice statement (cps). Your private key is a unique secret number that only you know. Public key authentication is a way of logging into an ssh/sftp account using a cryptographic key however, using public key authentication provides many benefits when working with multiple.
Public Key Erstellen: Der erste schritt bei der einrichtung openvpn ist eine zu erstellen public key infrastructure (pki).
Tidak ada komentar:
Posting Komentar